Security operations don’t just need to scale. They need to evolve. And that means replacing brittle rules with systems that learn, respond, and improve—on their own.
Let’s be honest—static playbooks aren’t enough anymore. You can’t write a workflow for every edge case. Threats change. Your infrastructure changes. And every incident teaches you something that gets lost in the backlog.
But what if your detection and response system actually learned from every incident?
This is the power of a closed-loop architecture for autonomous SecOps—one that turns your operations pipeline into a self-improving engine.
🧠 The Mental Model: From Pipeline to Feedback Loop
Most SOC pipelines today look like this:
Log ingestion → Detection → Alert → Analyst Review → Playbook → Resolution
Linear. Manual. Fragile.
Here’s the upgraded loop:
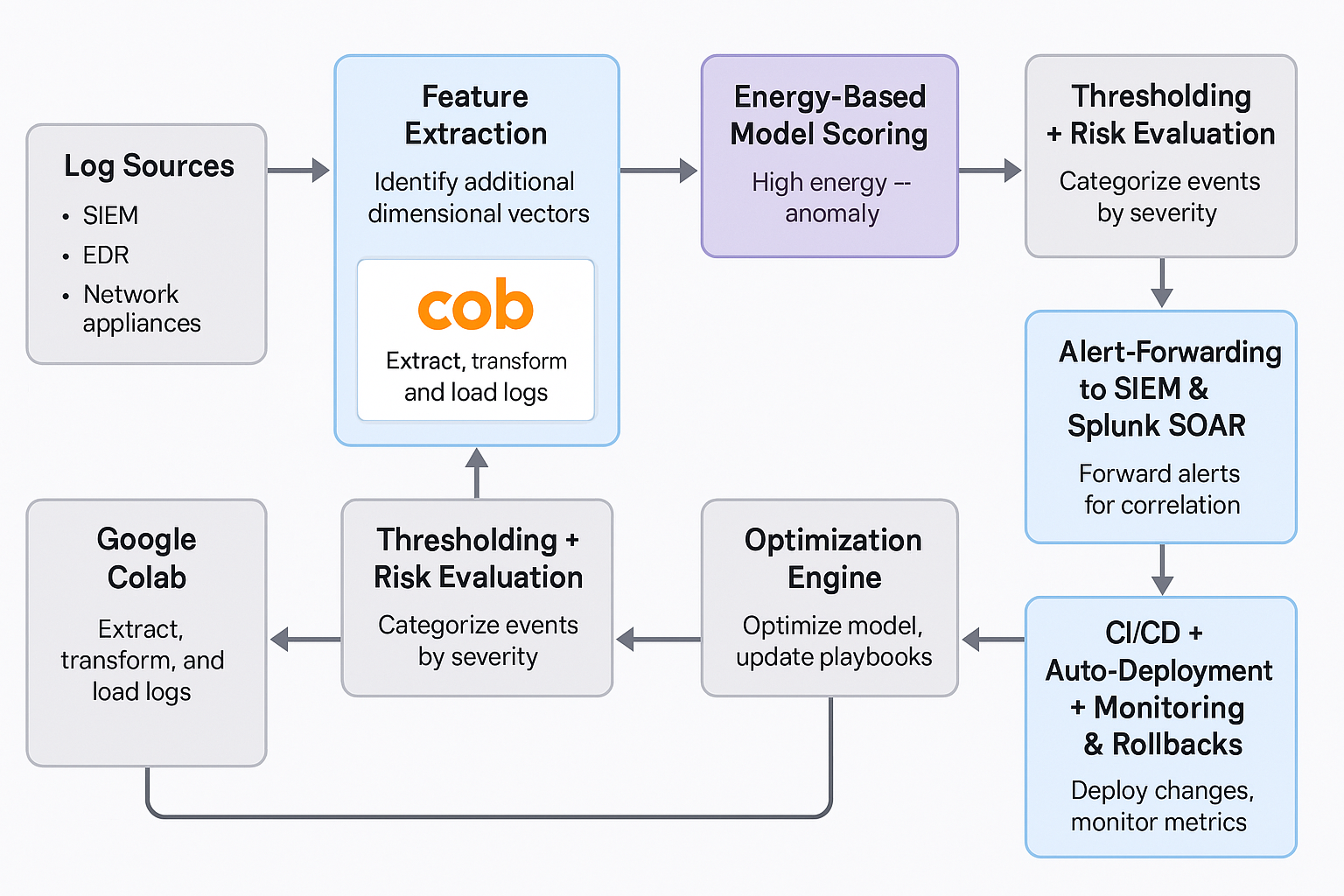
Engineer Self-Service → ETL + Schema Inference → EBM Detection → SOAR Playbook Mgt. → Result Logging → Simulation & Testing → Optimization Engine → Back to Detection
It’s not just automated—it’s reflexive. Every action leads to new data. Every mistake leads to a model or playbook improvement. The system doesn’t just run—it learns.
🛠️ What’s Inside the Loop?
✅ Step 1: Engineer Self-Service Onboarding
When a new service or app is launched, the engineer registers their log source via a lightweight UI or API. No need for predefined schemas. The logs are routed into the system and staged for analysis.
🔍 If the engineer doesn’t know the schema?
No problem. The ETL pipeline automatically infers structure and extracts dimensional vectors.
✅ Step 2: ETL & Feature Engineering
Google Colab or other ETL backends clean, transform, and enrich the logs dynamically—turning raw text into structured event vectors.
✅ Step 3: EBM Scoring
An energy-based model analyzes every event and assigns an anomaly score. Events with high “energy” deviate from learned normal behavior.
✅ Step 4: SOAR Playbook Creation & Execution
For high-risk events, the system auto-triggers a playbook creation and / or optimization that performs containment, enrichment, escalation, eradication—or all four.
✅ Step 5: Simulation & Feedback
Synthetic threats are injected to validate the entire pipeline. Did the right detection trigger? Did the playbook behave as expected?
✅ Step 6: Optimization Engine
A reinforcement learning (RL) agent or genetic algorithm proposes improvements to detections and playbooks based on failure cases or drift.
| Contribution | Innovation |
|---|---|
| Self-Service Log Onboarding | Reduces security friction in DevOps pipelines |
| Schema Inference in ETL | Enables true zero-touch log ingestion |
| Energy-Based Model Scoring | Improves anomaly detection with better uncertainty modeling |
| Closed-Loop Playbook Creation & Optimization | Adapts responses based on performance, not just static logic |
| CI/CD for Playbooks | Treats security automation as code—tested, versioned, deployed automatically |
or another workflow suiting ITIL based institutions may look like the following;
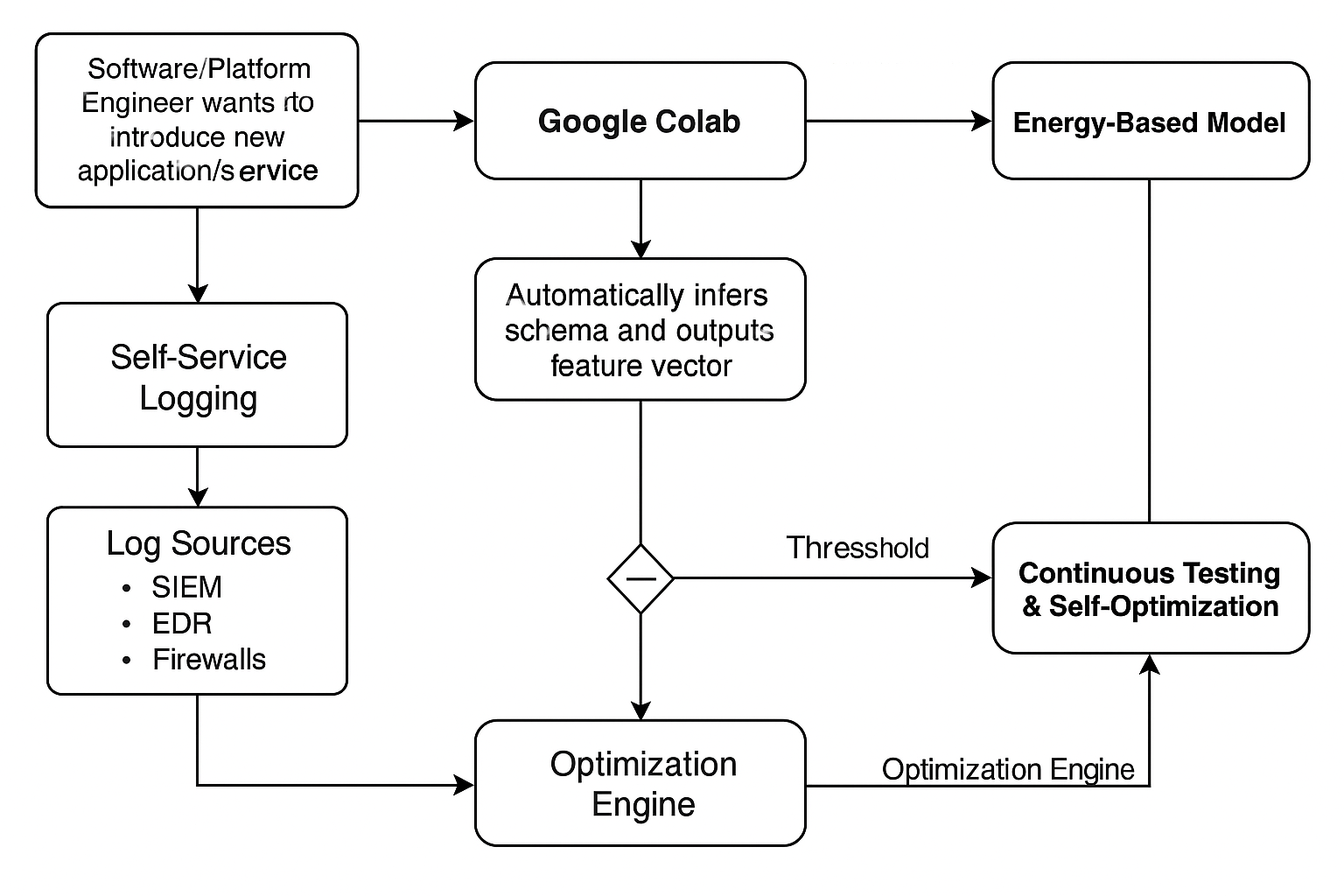
If you didn’t want the self-service workflow
For instance, you operate within a COBIT environment
🔍 Real Example: Playbooks That Improve Themselves
In a recent environment, simulated insider threat behaviors were introduced into the pipeline weekly. The optimization layer:
- Flagged playbooks that missed high-energy detections
- Proposed logical changes (e.g., new conditions, reduced timeouts)
- Validated changes through simulation
- Automatically promoted successful improvements
The result? Mean time to response dropped 57%—without a single new rule manually written.
🤖 Why Static Systems Break Under Pressure
Traditional SOC architectures break because:
- Detection rules go stale
- Playbooks grow unmanageable
- Incident learnings get lost in Slack threads
An autonomous loop solves this by:
- Learning from what’s normal—and what’s not
- Continiously refining playbooks
- Using feedback from real incidents and tests to evolve
🎯 Your Move
If you’re still maintaining brittle playbooks by hand, ask yourself:
What if the system could evolve them for you—and every new service onboarded itself?
👉 Get in the loop. Automation is step one. Autonomy is the future. Read the full white paper or dive into the latest podcast episode to learn more.
