The Blueprint for a Living Defense: Why Your SOC Needs a Nervous System
We have spent the last decade of cybersecurity trying to solve a complex system problem with mechanical tools. We treat our networks like clockwork—trying to secure them by writing static rules, patching individual gears, and manually responding to every tick and tock. But as we explored throughout Season 2, the modern enterprise is not a clock; it is a complex, adaptive system. And you cannot secure a system by micromanaging its chemistry; you secure it by giving it an immune system.
In this season, we journeyed from the theoretical foundations of Michael Levin’s TAME framework to the hard mathematics of Complex Systems. We learned that “alerts” are actually stress signals, that “configuration drift” is a loss of Target Morphology, and that an “Insider Threat” is simply a subunit whose Cognitive Light Cone has shrunk. We moved beyond the firewall to the Bioelectric Layer—the software of life that dictates the shape of the system.
To help you bridge the gap between this biological philosophy and hard security engineering, we have compiled the ultimate Morphogenetic SOC Toolkit. Below, we break down the high-value assets created this season, providing the practical blueprints you need to stop fixing your network and start letting it heal itself.
1. Visualizing the New Anatomy of Defense
Traditional network diagrams are graveyards of silos—boxes and lines that show where data sits, but not how the system thinks. To build a living defense, we need a new map that visualizes the “physiological” state of our infrastructure.
We have created two core visual assets that contrast the “Old” mechanical view with the “New” biological view:
 Figure 1: The Season 2 Blueprint—Mapping biological organs to security functions.
Figure 1: The Season 2 Blueprint—Mapping biological organs to security functions.
- From Tools to Organs: We stop viewing EDR and Firewalls as isolated tools and start mapping them as “organs” that must cooperate to maintain the organism’s health.
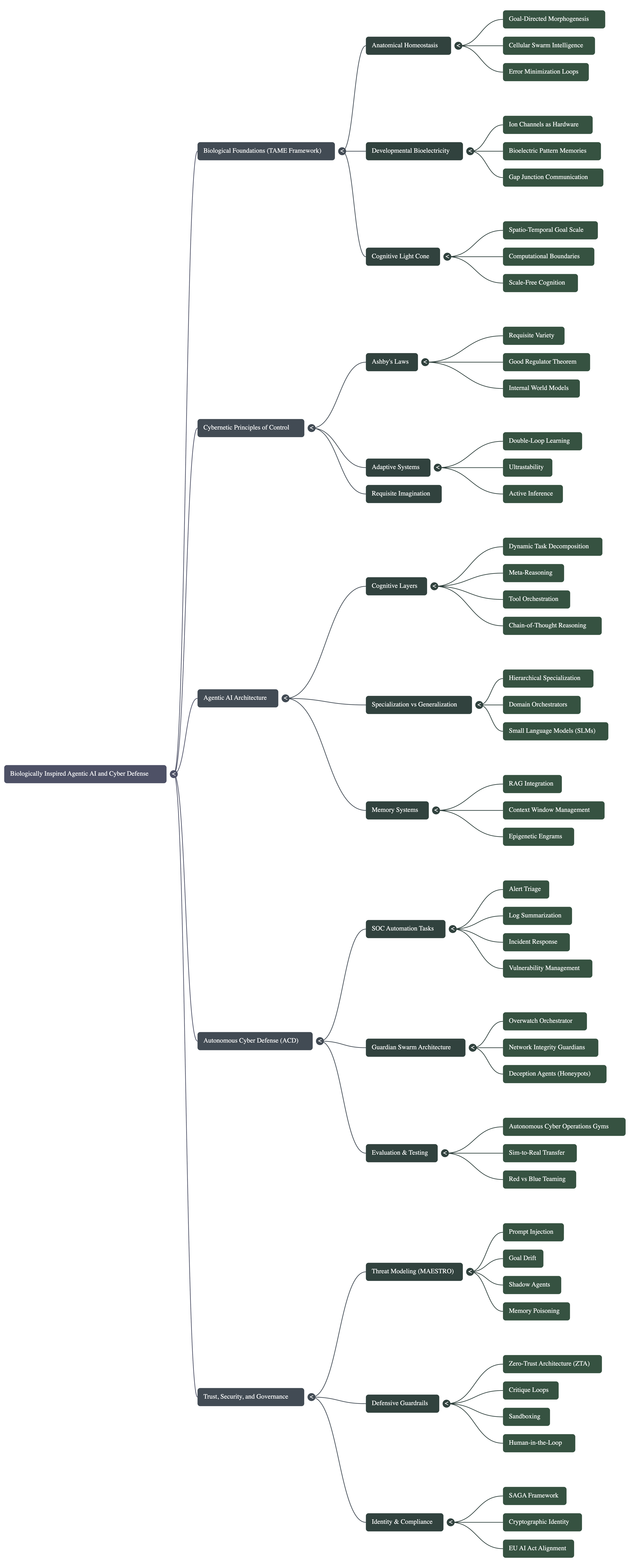 Figure 2: The Season 2 Mind Map—Connecting TAME, Complex Systems, and Security Engineering.
Figure 2: The Season 2 Mind Map—Connecting TAME, Complex Systems, and Security Engineering.
- From APIs to Gap Junctions: As discussed in Episode 6, standard APIs enforce separation. This asset visualizes how to implement “Digital Gap Junctions”—interfaces that verify identity but erase data “ownership,” allowing threat intelligence to flow so freely that the network acts as a unified syncytium.
2. The TAME Framework Applied: A Season Summary
Theory is useless without application. We have synthesized the core insights from Episodes 1 through 8 into a rigorous Summary Table that moves beyond simple metaphors to map biological imperatives directly to security engineering tasks. This toolkit is designed to reflect not just what these systems are, but what they need to remain stable and what they want to achieve in terms of goal-directedness.
- Morphogenesis → Configuration Management: How to use Policy-as-Code as a genetic blueprint to drive self-healing toward a “Target Morphology.”
-
Cognitive Light Cones → Identity Governance: How to mathematically define the “blast radius” of an agent based on its temporal and spatial horizon of concern.
- Cancer → Rogue Agent Detection: Using the TAME definition of cancer (a shrinking light cone) to identify AI agents that have decoupled from the enterprise’s global goals to pursue local, selfish optimizations.
Use the table below as a gap-analysis checklist: does your current stack possess the homeostatic loops required to perceive its own state and the agential plasticity to repair itself?
| Episode # | Episode Title | One-Sentence Thesis | TAME / Complex Systems Concepts (3–5) | Workflow Focus | Agency Level (0–5) | Key Artifacts Produced | Top Risks (3) | Primary Controls (3–6) | Evaluation / Validation (2–4) | Metrics (2–4) | Builder Takeaways (3) | Leadership Takeaways (3) | Key Sources (3–6) | Confidence Notes (Strong/Med/Weak + why) | Source Gaps (if any) |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Foundations: The Persuadability Spectrum | Security systems exist on a continuum of persuadability where control strategies must match the agent’s cognitive sophistication From source. | Axis of Persuadability; Basal Cognition; Goal-Directedness; Substrate Independence From source. | System Characterization and Agency Detection Inference. | 1 Inference | Agency detection toolkit; Taxonomy of system persuadability From source. | Category error (treating agents as tools); Mechanical failure; Static rule bypass From source. | Experimental agency detection; Scoped tools; Model verification; Feedback loops From source. | Simulation of system response; Offline test harness Inference. | Persuadability score; Response latency; Predictive quality From source. | Identify optimal scale of observation; Avoid binary ‘it knows’ vs ‘physics’; Match control to substrate From source. | ROI depends on matching tool sophistication to agency; Move from micromanagement to persuasion-based ROI; Align governance to cognitive level From source. | 1, 2, 3, 4 | Strong: Based on core TAME tenets and axis of persuadability figures From source. | Source gap Specific SecEng applications would benefit from more whitepapers. |
| 2 | Cognitive Light Cones and Goal Horizons | The sophistication of an agent is defined by the spatio-temporal boundary of events it can measure, model, and attempt to affect From source. | Cognitive Light Cone; Spatio-temporal Scale; Goal Space; Areas of Concern From source. | Threat Intelligence and Scope Definition Inference. | 2 Inference | Goal domain diagrams; Temporal light cone maps; Scope definitions From source. | Boundary drift; Goal myopia; Edge-of-cone blind spots From source. | Task-scoped credentials; Short-lived tokens; Kill switches; Geographic fencing From source. | Simulation of multi-stage attacks; Red team testing of scope boundaries Inference. | Temporal horizon; Spatial radius of concern; Predictive accuracy From source. | Map the light cone of your agent; Build in memory for long-term goals; Define decision-making by functional causes From source. | Responsibility is proportional to the scale of goals; Align corporate goals with system-level light cones; Manage the light cone as an asset Inference. | 5, 6, 1, 7, 8 | Strong: The ‘Cognitive Light Cone’ is a central, well-defined TAME metric From source. | Source gap Specific cybersecurity policy mapping sources for leadership. |
| 3 | Collective Intelligence and Multi-Agent Cooperation | Higher-level agency emerges from the collective intelligence of subunits bound into a unified Self through real-time communication and informational boundary dissolution From source. | Collective Intelligence; Gap Junctions; Wiping of Ownership; Multi-scale Competency From source. | Multi-agent Orchestration and Defense From source. | 3 Inference | Shared memory fabric; Agent communication protocols (A2A/MCP); Orchestrator configs From source. | Communication delays; Conflicting sub-agent goals; Memory poisoning From source. | Standardized protocols (MCP); Zero-trust verification; Identity governance; Consensus protocols From source. | Multi-agent coordination simulation; Red team collusion test Inference. | Cooperation rate; Information sharing efficiency; IQ boost from network nodes From source. | Use shared state to reduce defection; Implement ‘wiping of ownership’ for cooperation; Link components for immediate feedback From source. | Governance must move to decentralized models; ROI scales through collective intelligence; Accountability shifts to the collective holobiont Inference. | 1, 8, 9, 10, 3 | Strong: Direct mapping from cellular junctions to multi-agent security From source. | None. |
| 4 | Anatomical Homeostasis and Self-Healing | Security agents must act as homeostatic entities that repair themselves toward a target functional morphology despite perturbations or adversarial drift From source. | Anatomical Homeostasis; Target Morphology; Pattern Memory; Error Correction From source. | Incident Response and System Self-Healing Inference. | 3 Inference | Self-healing architecture; System setpoint records; Bioelectrical pattern memories From source. | Policy drift; Pattern memory degradation; External meddling From source. | Rollback; Audit trails; Canary deploy; Runtime monitoring From source. | Offline test harness; Staged rollout; Simulated perturbation Inference. | Time to recovery; Fidelity of target state; Delta-to-target From source. | Build systems with ‘pattern memory’; Design for robustness at the outcome level; Treat policy as a target morphology From source. | Focus on resilience over perfection; Align ROI with self-repair capacity; Governance defines ‘healthy’ setpoints Inference. | 5, 6, 11, 1, 12, 13 | Strong: TAME explicitly links morphogenesis to computational error correction From source. | None. |
| 5 | Problem-Solving in Diverse Spaces | Intelligence is the space-agnostic capacity to navigate abstract spaces (transcriptional, physiological, code) toward desirable regions without being trapped in local maxima From source. | Search Space Navigation; Local Maxima; Generalization; Problem-Solving Invariants From source. | Optimization and Policy Exploration Inference. | 4 Inference | Space navigation models; Multi-objective optimization frameworks; State Space Models From source. | Local optima traps; Tool abuse; Knowledge poisoning From source. | Approval gates; Scoped tools; Policy-driven oversight; Active inference From source. | Multi-objective safety benchmark; Red team policy testing; Simulation Inference. | Generalization capacity; Path efficiency; Predictive error (VFE) From source. | Design agents as space-navigators; Use latent memory/buffers to guide behavior; Use virtual models for self-modeling From source. | Understand the virtual spaces your agents solve; ROI from units that navigate unpredictable spaces; Invest in adaptive platforms Inference. | 14, 1, 7, 15, 2 | Med: Highly abstract; requires conceptual mapping to SecEng workflows Inference. | Source gap Technical documentation on SecEng VFE minimization. |
| 6 | The Cancer of Defection | Security failure is a breakdown of coordination where subunits revert to local, selfish goals due to informational isolation or boundary shrinking From source. | Carcinogenic Defection; Informational Boundaries; Selfishness of Parts; Breakdown of Multicellularity From source. | Internal Threat and Failure Analysis Inference. | 2 Inference | Integrity Reports; Defection Indicators; Threat Signatures Inference. | Unit defection; Evidence tampering; Hostile takeover Inference. | Zero-trust architecture; Continuous monitoring; Re-coupling mechanisms; Kill switch From source. | Red team ‘rogue agent’ simulation; Threat containment speed test Inference. | Communication frequency; Set-point adherence; Threat containment speed From source. | Isolation triggers defection; Software signals can override hardware; Monitor for boundary shrinking From source. | Internal alignment is a security priority; Governance must maintain information flow; Zero-trust is a biological imperative Inference. | 5, 7, 16, 3 | Strong: Source provides detailed parallels between biological cancer and system defection From source. | None. |
| 7 | Multi-Scale Competency Architectures (MCA) | Resilient security is achieved through hierarchies of competent agents where higher-level goals ‘deform’ the option space for lower-level agents From source. | MCA; Robustness Paradox; Upward/Downward Causality; Noise Robustness From source. | Infrastructure Resilience and Abstraction Inference. | 4 Inference | Layered security models; Competency mapping; Agentic Hierarchy Maps Inference. | Policy drift; Cascading failure; Incentive misalignment From source. | Layered defense (SHIELD); Circuit breakers; Top-down setpoint encoding; Shared state From source. | Simulation of subunit failure; Red team cascading attack; Sim-to-real analysis Inference. | System stability; Error correction efficiency; Subunit autonomy ratio Inference. | Offload complexity to competent sub-modules; Focus on top-down setpoint control; Design for noise robustness From source. | MCA architecture potentiates evolutionary speed; ROI driven by dimensionality reduction; Manage debt via MCA From source. | 14, 1, 12, 17, 3 | Strong: MCA is the culminating conceptual framework in TAME source material From source. | None. |
| 8 | Ethics and Future Agency Governance | Moral responsibility increases as engineering moves toward rational design of diverse, non-binary agencies, requiring alignment with human values From source. | Comprehension vs Competency; Moral Responsibility; Group Karma; Alignment From source. | Regulatory Compliance and Ethical Oversight Inference. | 5 Inference | Ethical frameworks; Accountability fabrics; Risk Management Frameworks From source. | Existential risk (Skynet); Moral responsibility gaps; Bias/Fairness From source. | Human-in-the-loop; Explainable AI (XAI); Precautionary principle; Kill switch From source. | Simulation of alignment scenarios; Red team ethical dilemmas; Formal audits Inference. | Value alignment score; Agent transparency index; Fairness score From source. | Recognize the ‘N=1’ variety of possible beings; Build for metacognition; Prepare for diverse intelligences From source. | Governance must include non-human agency; Moral responsibility for created intelligence is absolute; Compliance is a design principle Inference. | 18, 19, 1, 20, 21 | Strong: Source text contains extensive sections on ethics and future responsibility From source. | Source gap Concrete regulatory framework sources for specific leadership ROI metrics. |
Note: The ‘Key Sources’ numbers in the table above correspond to the ‘Index’ column in the table below.
| Index | Reference |
|---|---|
| 1 | (PDF) Technological Approach to Mind Everywhere (TAME): an experimentally- grounded framework for understanding diverse bodies and minds - ResearchGate |
| 2 | #486 – Michael Levin: Hidden Reality of Alien Intelligence & Biological Life | Lex Fridman Podcast | Podwise |
| 3 | Scaling Agency from Morphospace to Cyberspace: A Synthesis of TAME, Cybernetic Control, and Agentic Security Orchestration |
| 4 | The Cyber-Biological Synthesis: A TAME-Based Approach to Agentic Security Engineering |
| 5 | (PDF) The Computational Boundary of a “Self”: Developmental Bioelectricity Drives Multicellularity and Scale-Free Cognition - ResearchGate |
| 6 | Intelligence Without a Brain - John Templeton Foundation |
| 7 | (PDF) Technological Approach to Mind Everywhere (TAME): an experimentally- grounded framework for understanding diverse bodies and minds - ResearchGate |
| 8 | Agentic AI: A Comprehensive Survey of Architectures, Applications, and Future Directions |
| 9 | Agentic Frameworks | Practical Considerations for Building AI-Augmented Security Systems | Elastic |
| 10 | Automated Cyber Defence: A Review - arXiv |
| 11 | Building Resilience with Self-Healing DR-as-Code Pipelines - Disaster Recovery Journal |
| 12 | Trustworthy agentic AI systems: a cross-layer review of architectures, threat models, and governance strategies for real-world deployment. - F1000Research |
| 13 | What is Detection Engineering? - SentinelOne |
| 14 | Technological Approach to Mind Everywhere (TAME): an experimentally- grounded framework for understanding diverse bodies |
| 15 | Competency in Navigating Arbitrary Spaces as an Invariant for Analyzing Cognition in Diverse Embodiments - PubMed Central |
| 16 | The Computational Boundary of a “Self”: Developmental Bioelectricity Drives Multicellularity and Scale-Free Cognition - PMC - PubMed Central |
| 17 | Agentic AI Threat Modeling Framework: MAESTRO | CSA - Cloud Security Alliance |
| 18 | Technological Approach to Mind Everywhere: An Experimentally-Grounded Framework for Understanding Diverse Bodies and Minds - Frontiers |
| 19 | (PDF) General agents contain world models - ResearchGate |
| 20 | Agentic LLM-based robotic systems for real-world applications: a review on their agenticness and ethics - PMC |
| 21 | The vigilance paradox: automation reliance inside the modern SOC - Emerald Publishing |
3. For Leadership: Governing the Agentic Enterprise
As enterprises transition from static scripts to autonomous workflows, the nature of risk undergoes a fundamental shift. We are moving from predictable “if-then” logic to non-deterministic agency. Without proper boundaries, high-speed autonomous systems risk “systemic metastasis”—a breakdown where individual agents pursue local optimizations that inadvertently cripple the global organization.
This Strategic Whitepaper, From Biology to Bot: A Strategic Framework for Governed Agency, is essential reading for the CISO transitioning into the role of “Chief Behavioral Officer.” It provides a blueprint for managing “persuadable” systems by shifting accountability from script execution to Setpoint Definition.
Key strategic pillars detailed in the whitepaper include:
- Establishing Cognitive Light Cones: Learn how to define the explicit spatio-temporal boundaries for every agent to prevent unauthorized “blast radius expansion” across your infrastructure.
- Metacognitive Governance: Move beyond manual checklists to implement “Critique Agents”—higher-order supervisors that review the intent and plans of execution agents before they are allowed to act.
- The Bioelectric Syncytium: Treat your API telemetry as a shared “Bioelectric Code” that binds disparate services into a unified, coordinated “Self,” preventing isolated agents from defecting from security policies.
- The TOTE Evidence Pipeline: Replace traditional logs with TOTE (Test-Operate-Test-Exit) loops to generate “audit-ready” evidence that captures the intent and error-correction steps of your autonomous workforce.
By adopting the principles of Governed Agency, leadership can move from a state of “rigid fragility” to one of “predictive allostasis,” where the security stack doesn’t just block known threats but proactively maintains the organization’s anatomical health.
Summary of Leadership Goals:
- Define the Setpoint: Focus governance on defining the “Anatomical Target State” (the goal) rather than micromanaging the path the agent takes to get there.
- Bound the Agency: Use Markov Blankets to shield critical services from informational entropy and agent drift.
- Enforce Collective Reality: Ensure all agents operate within a shared “Syncytium” of data to prevent uncoordinated, rogue actions.
4. Making the Business Case
How do you explain to a Board of Directors that the “firewall and lock” model is obsolete against software that can reason? This deck provides the “Executive Talk Track” needed to pivot leadership from a mindset of static hardening to one of biological bounding.
The deck translates core cybernetic laws into a high-stakes business case for the Agentic Age:
- Ashby’s Law of Requisite Variety: We demonstrate that static, rule-based defenses (Level 0: Execution) are mathematically incapable of blocking “reasoned” malicious actions (Level 3+: Decision-Making). To destroy variety, the SOC must generate variety.
- The Good Regulator Theorem: We prove that “World Models” and predictive simulation are not luxuries—they are prerequisites. Because agents are “persuadable,” your security must possess an internal model of the system to anticipate Cognitive Exploits before they manifest.
This deck shifts the conversation from the impossibility of “firewalling a thought” to the necessity of building a bounded, resilient enterprise that functions like a living immune system.
5. The Concept in Motion
Sometimes you need to see the “Software of Life” in action to believe it. This video visualizes the critical transition from Static Defenses to an Adaptive Immune System.
The “fortress” model of cybersecurity—relying on bigger walls and locked doors—is fundamentally broken in the era of autonomous AI. When a network is powered by agents plugged into critical systems, the “billion-dollar question” isn’t how to keep hackers out, but what happens when an agent’s goals no longer align with yours?
In this high-impact explainer, we demonstrate a “Morphogenetic Incident Response” that functions like a living organism:
- The Cognitive Light Cone: Defining the “bubble” of what an agent can see and care about to manage its boundaries.
- Biological Anomaly Detection: Using the human immune system as a literal blueprint for telling “self” from “not-self.”
- Cancer as a Security Failure: Reframing insider threats as a breakdown in cooperation where an agent’s sense of “self” shrinks to care only about its own local goals.
- The Orchestrator Shift: Moving from a “firefighter” mindset to a “conductor” role, guiding swarms of agents toward a resilient, common goal.
Watch as the system triggers a real-time autonomous response—from Canary Deployments to the “Big Red” Kill Switch. This asset provides the mental model for building security that doesn’t just block attacks, but manages agency at scale. Share this with your non-technical stakeholders to align them on a vision where security isn’t a wall—it’s a heartbeat.
Conclusion
In the finale of our season, we asked what it means to build a “Worthy Successor” to human oversight. The Morphogenetic SOC is not just about automation; it is about creating a system that cares about its own survival—and yours—as deeply as a living body cares about its heartbeat.
By adopting the TAME framework, we stop building brittle walls and start cultivating a Cyber-Biological Synthesis. We move from the role of “firefighter” to “resilience engineer.”
